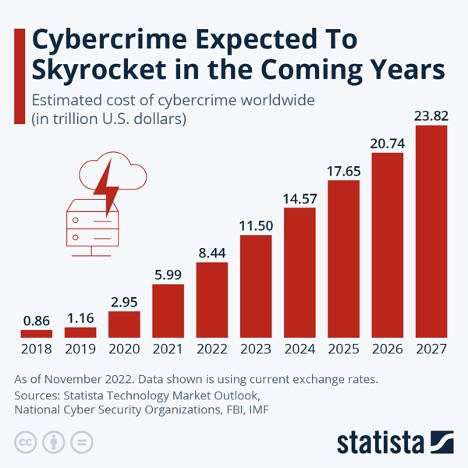
Microsoft’s December Patch Tuesday update delivers 59 fixes, including two zero-days (CVE-2022-44698 and CVE-2022-44710) that require immediate attention on the Windows platform. This is a network-focused update (TCP/IP and RDP) that will require significant testing with an emphasis on ODBC connections, Hyper-V systems, Kerberos authentication, and printing (both local and remote). Microsoft also published an urgent out-of-band update (CVE-2022-37966) to address serious Kerberos authentication issues.
Known issues
- ODBC: After installing the December update, applications that use ODBC connections through Microsoft ODBC SQL Server Driver (sqlsrv32.dll) to access databases might not connect. You might receive the following error messages: “The EMS System encountered a problem. Message: [Microsoft] [ODBC SQL Server Driver] Unknown token received from SQL Server”.
- RDP and Remote Access: After you install this or later updates on Windows desktop systems, you might be unable to reconnect to (Microsoft) Direct Access after temporarily losing network connectivity or transitioning between Wi-Fi networks or access points.
- Hyper-V: After installing this update on Hyper-V hosts managed by SDN-configured System Center Virtual Machine Manager (VMM), you might receive an error on workflows involving creating a new Network Adapter (also called a Network Interface Card or NIC) joined to a VM network or a new Virtual Machine (VM).
- Active Directory: Due to additional security requirements in addressing the security vulnerabilities in CVE-2022-38042, new security checks are implemented on domain net join requests. These extra checks may generate the following error message: “Error 0xaac (2732): NERR_AccountReuseBlockedByPolicy: An account with the same name exists in Active Directory. Re-using the account was blocked by a security policy.”
About Columbia Advisory Group:
Columbia Advisory Group (CAG) is a leading Information Technology (IT) consulting firm. CAG’s team has assessed and helped improve the performance of more than 300 technology organizations and IT departments, including many higher education institutions, state agencies, and Fortune 50 customers. Practice specialty areas include Infrastructure, IT Service Management, Cybersecurity, and A/V Services. CAG improves business outcomes with IT insights and expert technical support. Based in Dallas, Texas, CAG works extensively with clients throughout the U.S. Contact us at info@columbiaadvisory.com.

Brad Hudson
VP of Cyber Security | vCISO
CISSP,CCSP,CCNP,MCSA,MCITP:EA,SA